Update 02.07.2008: MacOS X 10.5.4 is out now. See our notes here.
I. Abstract
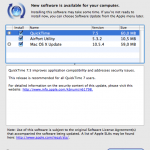
Three days ago (May, 28th) Leopard update 10.5.3 has been released. It solves several security issues and application issues (read details here). So sumed up: you should update. Being on a Hackint0sh we need to take some things into consideration because we cannot use the built-in auto update.
The following article shows how to upgrade your Intel based Hackintosh to version 10.5.3. The approach is pretty much the same like updating to 10.5.2 and can be applied to both updates.
One limitation: the whole update process is currently only applicable to close-to-original-mac-hardware and is being done manually. Note: we did not test this on AMD based Hackintoshs.
Note to first timers: after having installed the update. The updater asks you to reboot. Do not hit the restart button eventually, instead read on. Some more steps need to be applied before you are allowed to reboot. Don’t say, we didn’t warn you!
II. Enable root user
In case you did not enable root user access to your system yet, this is a good time to do that. This has been described a thousand times elsewhere, so we won’t delve into this too deep:
- Open
Directory Utility.app
- click the
Lock to allow changes (!)
- then
Edit > Enable root user > supply password of your choice
III. Obtain update package
For manual update we need to get the updater.
IV. Back up important data and custom kexts
Backup important data like
- documents
- emails
- muzaq
- videos
- downloads etc.
Don’t say we didn’t warn you in case anything goes wrong for whatever reason. After having done the backup of your personal data, do the backup for your system specific kexts.
Most simple way is using a terminal. Do the following:
hackint0sh$ su
(provide root password)hackint0sh$ cp -r /System/Library/Extension/KEXT-I-WANNA-BACKUP /TARGET/FOLDER/KEXT-I-WANNA-BACKUP
That kexts might be:
- Audio
- LAN
- WLAN
- Graphics Adapter etc.
This highly depends on your hardware. I am running an ASUS P5LD2 VM DH with a Sapphire HD 2600 XT. In my case I only need to backup my Natit.kext device driver and dsmos.kext, because history taught me a strange lesson once.
V. Use monitoring script
Since AppleIntelCPUPowerManagement.kext would simply kill our systems we need to make sure it does not become loaded into the kernel. So netkas supplied a little command line, which monitors the install of that file and if found removes it. You need to be logged in as root:
hackint0sh$ while sleep 1 ; do rm -rf /System/Library/Extensions/AppleIntelCPUPowerManagement.kext ; done
This command line must run until the end of the update.
VI. Process the update
Just mount your downloaded MacOSXUpdCombo10.5.3.dmg and begin your update. When the update process is complete
! ! ! ! _ d o n ‘ t _ i n s t a n t l y _ c l i c k _ r e s t a r t _ ! ! ! !
Instead of restarting, stop the while command line from step V. Stop it by hitting CTRL and C and read on, but don’t restart your system, until we say it.
VII. Modify startup script
Sadly, we are not running OS X on original hardware. The consequence is we are missing a chip for the fan control that holds a specific key (Alexander Graf told about the details here – german only). This key is necessary to run the graphical interface Aqua of Mac OS X (in fact: this key decodes the binaries – details about the binary protection are provided by Amit Singh here).
To make a long story short: we don’t want the operating system to look for that specific chip and key, we can supply it easier (via emulator). Netkas provided the emulator called dsmos.kext (kernel extension) for that problem as well.
Simply do the following (I assume you know how to use nano, you can also use vi or whatever you prefer).
hackint0sh$ nano /System/InstallAtStartup/scripts/1
In that 1 file there must be a line of code like this (old)
/System/Library/Extensions/Dont Steal Mac OS X.kext
This needs to be changed to this (new):
/System/Library/Extensions/dsmos.kext
Then save and exit. Using nano simply click CTRL and X, you will be asked if you wanna save before exiting.
VIII. Restoring kexts
We highly recommend you are logged in as root on a command line. In step IV. you saved your specific kexts. Now is the time to recover them to this folder:
/System/Library/Extensions
We will not explain how to use the copy command: this is the learning curve for today 8-))
IX. Reboot your machine
After having restored your system specific kexts. You reboot your machine. On first reboot, screen will not show the GUI but will show a black screen for about 3 minutes. It will then reboot again and it will take about 3 minutes again to show you the GUI (in our case the login window).
Shouts fly out to Netkas who’d better call himself +netkas and to Davil Elliott ;-) Live long and prosper, dudes!
And finally a word by our sponsor, who reduces our costs for this project at least a bit. Take them advertisments into consideration, would you? Thanks in advance!