A community around french hacker Mathieulh has provided information and assumptions of the PS Jailbreak’s bowels. Find the original article here and a PDF copy here.
Picture is courtesy of
PS3News.com…
Sniffed Code and Processing
As of yesterday they say they successfully managed to clone PS Jailbreak and they will document the exploit on the PS3 Wiki soon.
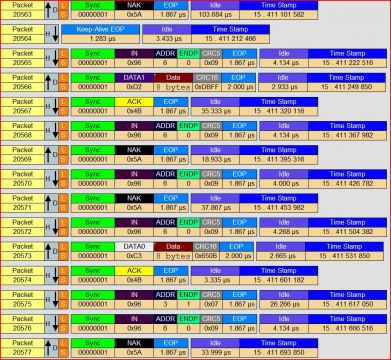
Moreover PS3News.com released the sniffed USB stream of the PS Jailbreak device:
(..) Descrambler sniffed the USB traffic and shared the log.(..)
- The PSJailbreak is inserted
- It connects with the host (PS3) and sends 09 02 12 00 01 00 00 80 + all the bytes from the first packet starting at 0008 up to 00EFF.
- The stack is overwritten and the PS3 jumps into code from the packet
- The Atmega sends a “USB Disconnect command”
- The last three steps are repeated four times
- It connects with the host and sends 09 02 4D 0A 01 01 00 80 + the bytes from the second packet starting at 0008 up to 0A4C
- The stack is overwritten and the PS3 jumps into code from the packet
- The Atmega sends a “USB Disconnect command”
- The last three steps are repeated twice.
Voilà… The PS3 is in “Debug Mode”.
Apparently the third and fourth byte of the after the 09 02 are the numbers of bytes to be sent. At least this goes for the second log (4D 0A->0A4D bytes)…
The first 8 bytes are from the usb protocol left [09 02 ... ]
The code will be pushed four times onto ps3 usb stack:
00000: 09 02 12 00 01 00 00 80 FA 09 04 00 00 00 FE 01
00010: 02 00 00 00 00 00 00 00 FA CE B0 03 AA BB CC DD
00020: 38 63 F0 00 38 A0 10 00 38 80 00 01 78 84 F8 06
00030: 64 84 00 70 38 A5 FF F8 7C C3 28 2A 7C C4 29 2A
00040: 28 25 00 00 40 82 FF F0 38 84 00 80 7C 89 03 A6
(..) this is a snipped only.
Find the whole sniffed hex code and asm readable code here and as 7zip downloadable archive here…
Our Comments
Well, this game is over. It’s pretty sure, that the commercial hackers have lost and so do the chinese clone makers. Even before the devices have been made available to the masses.
We suppose this might not have happened if Sony wouldn’t have disabled the Other-OS/Linux feature a couple of months ago. At that point only GeoHot and XorLoser were attacking the PS3 with a rather mass-incompatible but techie approach, that includes badly glitching technics.
Now this new bootloader exploit is known to the community. In fact, it is only a matter of days until a free open source solution will be available on the internet.